For the launch of the new password manager, Cozy Pass, Paul Tran-Van, Head of R&D and Data Scientist @Cozy Cloud has decided to get to the point of encryption. He will address some questions: How does the password manager work in your Cozy? What is its encryption protocol? In less than five minutes, encryption in Cozy will no longer hold any secrets for you and you'll be eager to get started: install Cozy Pass.
Definition
According to Wikipedia :
Encryption is the process of encoding a message or information in such a way that only authorized parties can access it and those who are not authorized cannot.
Let us introduce you an example of encryption with an exchange of messages between two correspondents.
- A clearly legible message is encrypted into a message that is incomprehensible to anyone who reads it. For example,
Hello Cozyis encrypted toWHa?&iehgzy8W9aehml5. - The encrypted message is sent to the recipient. If this message is intercepted, it will remain encrypted and therefore unreadable by an hacker.
- When it arrives at its destination, the recipient, and only the recipient, has a way to decrypt the original message:
Hello Cozy.
This way of protecting messages between recipients is not a new concept.
We can take as an example the Caesar Code, named due to the famous Roman Imperator. During the Gallic War, Caesar used an encryption system to transmit his messages: each letter was substituted by another, by a fixed offset in the alphabet. For example, Cozy with a shift of 1 gives Dpaz: C is transformed into D, o into p, etc.
Today's encryption systems are much more complex, but not so different. They are still based on two fundamental principles:
-
An encryption algorithm, i.e. the way the data will be transformed. In the case of the Caesar Code, it is the permutation of the letters of the alphabet.
-
An encryption key: the secret value that will be used by the algorithm to perform the encryption. In our example of the Caesar Code, the key is simply "1" and can take 26 different values, the size of the alphabet.
When Caesar encrypted his messages, security relied more on spies not knowing the algorithm than on the key. Indeed, once the algorithm is known, it is relatively easy to deduce the key from a message.
Today, in terms of security, we consider the opposite: the key is the root of security, while the encryption algorithm must be public so that it can be audited by experts.
There are usually different stages in an encryption system, with different exchanges of messages, and often several algorithms and keys used. This is known as the encryption protocol, which we detail here in more detail in the context of the password manager.
Data encryption
How does it work?
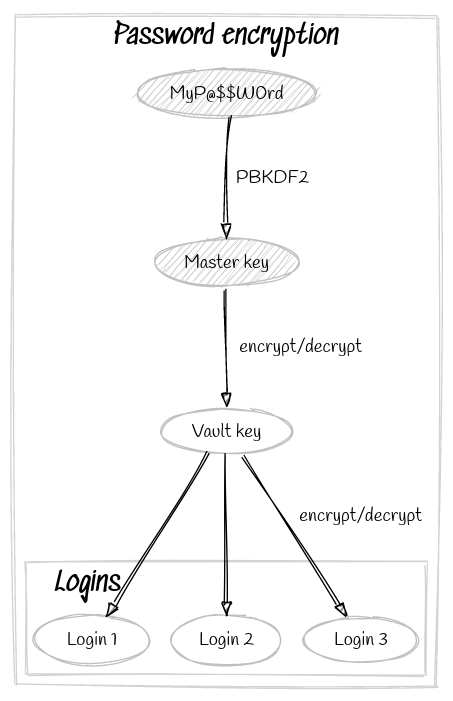
In your Cozy, the password manager is used for storing all your login credentials, payment cards and identities.
- When creating the Cozy password, an encryption key is derived from it by a sequence of mathematical operations. We name it the master key and is never stored. It is important to note that the password is never transmitted in clear text to the Cozy server, which therefore never knows this key.
- Another key is randomly generated and encrypted by the master key, which is called the vault key. This key remains stored encrypted in the database and will be used to encrypt all future keys. Again, the Cozy server never has access to it in clear text.
And what happens for the user?
-
When the user logs in to his password manager, the master key is recomputed from the Cozy password and the vault key is decrypted.
-
If the user adds a new login credential (username and password), it is immediately encrypted with the vault key.
-
The new encrypted credential is sent to the server that will store it, without having any way of knowing its content.
-
Each data managed by the password manager (login, credit card, identity) is thus retrieved from the Cozy server and decrypted in the application thanks to the vault key.
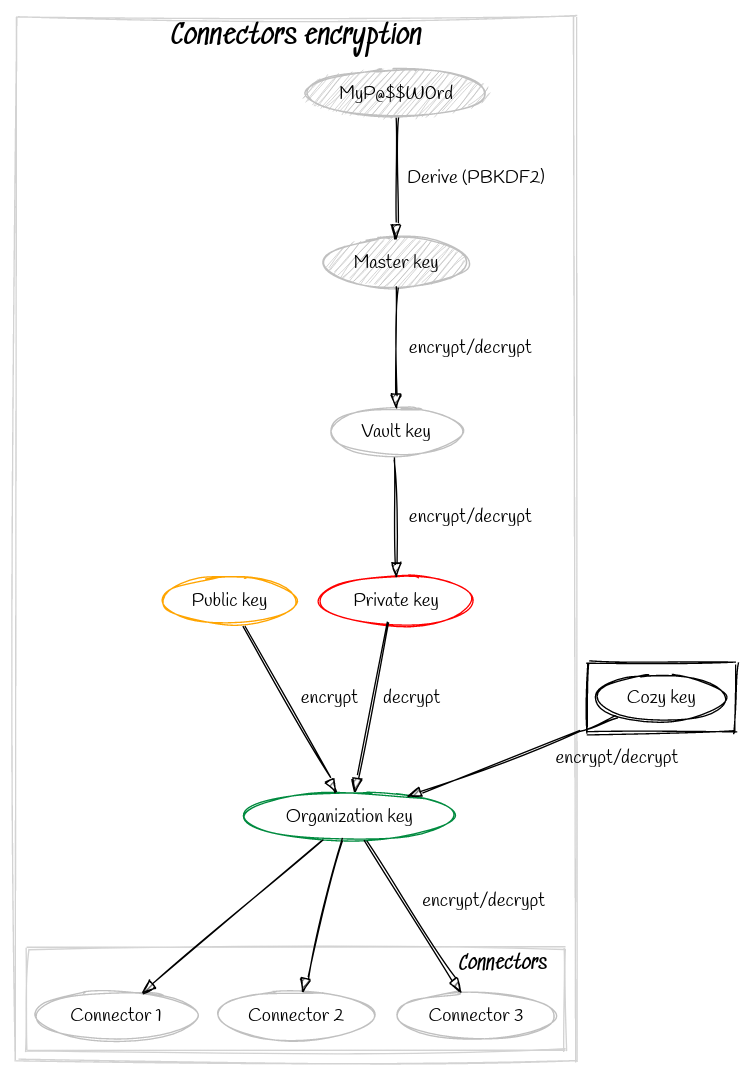
Specific case in your Cozy: connected services
In the case where credentials are used by a connector (=aims at retrieving data from an online service), a special encryption is set up. Indeed, it is necessary that the credentials (and only those) can be decrypted without any action from the user, in order to be able to automatically retrieve the data from your online services any time the user wants.
It is essential to specify here that the connectors are executed in an isolated and secure environment, which is the only one with the rights to decrypt the connectors' credentials.
To this end, we use a protocol named asymmetrical encryption :
-
A pair of keys are used: one is dedicated to the encryption and the other one only for the decryption.
-
Named as “public key” the encryption key that does not have to be protected, and “private key” the decryption key that has to be "secret". This one is stored in the password manager and encrypted with the vault key.
The encryption protocol of the connectors is as follows:
-
Once the Cozy password is created, a specific key is generated named as organization key. This key is shared between the Cozy server and the password manager and is used for the decryption of connectors.
1.1. The organization key is transmitted to the password manager by encrypting it with the public key. The organization is decrypted by the private key.
1.2. That key is also stored in the Cozy of the user, encrypted with a special key bound to an isolated environment that we name Cozy key.
-
Once a connector is created, the credentials are stored as encrypted with the shared organization key.
-
Once the connector is launched, the decryption of credentials is allowed thanks to the organization key, which is also decrypted by the Cozy key in an isolated environment.
-
All the credentials used by the connectors are reachable in the password manager and decrypted with the shared organization key.
What about Cozy Pass?
Today we are pretty proud of the new application available in your Cozy Cozy Pass, a fully integrated password manager based on the encryption protocol that we just explained above.
For Cozy Pass, we preferred to start from established protocols rather than reinventing the wheel. This is a guarantee of security for you.
For those reasons we have chosen to use open protocol of Bitwarden, reimplementing some of the software and adapting others.
With this integrated password manager, your passwords, payment methods and identities details are grouped and encrypted in your personal cloud so that you are the unique owner.
Your password manager simplifies and secures your passwords: no more post-it notes and "12345"!
At last, security goes hand in hand with simplicity:
- it automatically saves and fills in all your passwords when you browse the Internet;
- your passwords are now secure because they are all different, strong and stored encrypted;
- it synchronizes your passwords between your computers, browsers and phone: your passwords are at hand anytime, anywhere and up to date;
- it fills in one click the forms (name, first name, date of birth, credit card number, delivery address...);
- it imports your passwords already saved from another manager or browser.
Readings, links et resources
- More details about encryption in Cozy available on our Github page
- "Cryptographic introduction" written by Eric Daspet, CTO Cozy Cloud
- More about Ceasar Code
- Discover all the magic of Cozy on cozy.io and Cozy Pass






